75% of dating apps are unsafe, new study finds

Swiping right might seem like a harmless way to connect, but our latest analysis shows that most dating apps have a long way to go to reach A-grade cybersecurity.
The Business Digital Index (BDI) team analyzed the 24 largest dating platforms to assess how well they secure their digital infrastructure.
Unfortunately, 75% of major dating apps received a grade of D or F for their cybersecurity efforts.
This matters because dating apps store some of the most intimate data imaginable—private messages, sexual orientation, personal photos, even credit card information. When those systems fail, the consequences are devastating:
- In 2015, the Ashley Madison breach exposed data from over 30 million users, leading to broken marriages, blackmail, and even reports of suicides.
- In 2016, AdultFriendFinder was hit by one of the largest breaches in history: more than 400 million accounts leaked, including extremely sensitive sexual preference data.
- In 2018, a security company discovered that, due to lackluster encryption, it was possible to reconstruct someone's entire Tinder app experience.
- In 2019, on Valentine's Day, Coffee Meets Bagel admitted hackers had stolen the details of 6 million users, including email addresses and names, which were later sold on the dark web.
- In 2020, Zoosk was breached by the ShinyHunters hacker group, with up to 24 million records stolen—including personal data like income, birthdates, weight, political views, and sexual orientation.
- In 2024, researchers discovered that apps like Tinder, Bumble, Grindr, and Hinge all have API vulnerabilities that expose sensitive user data and allow threat actors to know users' precise location.
Given the frequency with which dating apps are targeted and the severe consequences of data leaks, the Business Digital Index team analyzed the most popular platforms to identify which, if any, can be trusted for their cybersecurity.
Here’s a summary of how the Business Digital Index measures companies' cybersecurity posture:
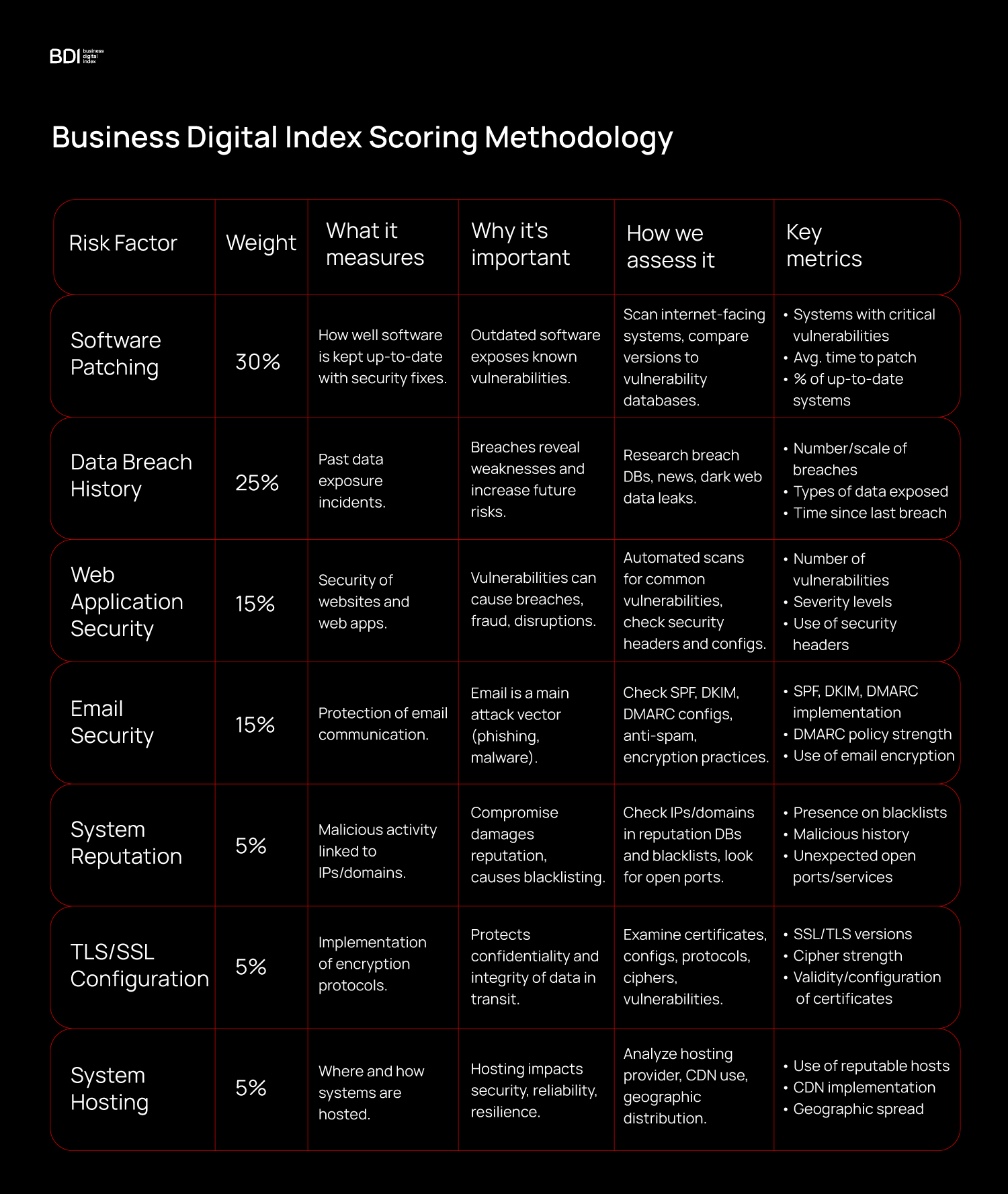
- Full technical methodology is available here.
- BDI carries out passive scans of publicly visible systems, no internal access required.
- Grading scale: 0–100 scores mapped to A–F grades.
Dating apps ranked by cybersecurity: best to worst
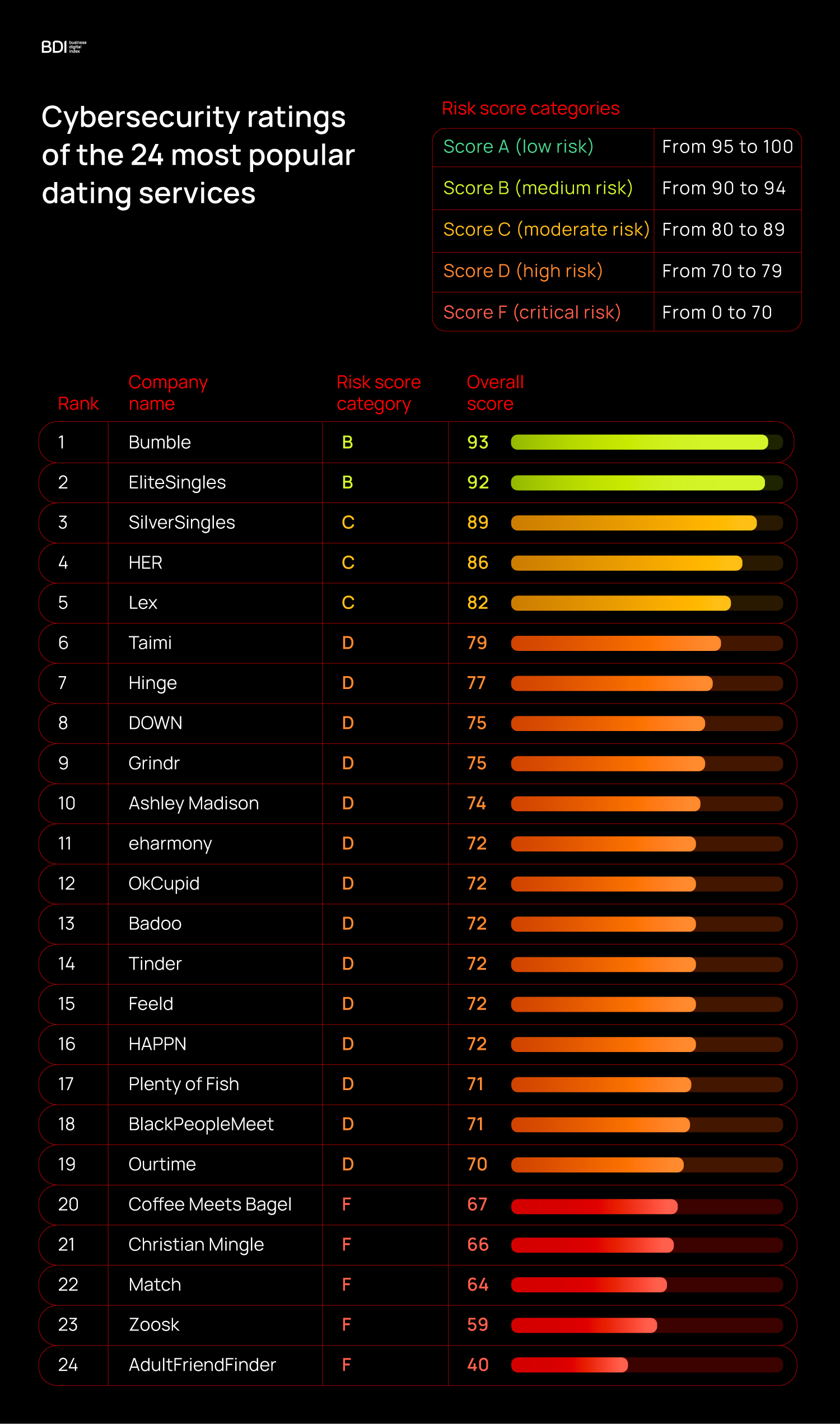
Best performers
Only two platforms reached the B category, which is the best result in this study.
- Bumble: Score 93, Grade B
- EliteSingles: Score 92, Grade B
Middle of the pack
The biggest household names fall here — secure enough to avoid outright failure, but not by much.
- C grade (80–89): SilverSingles (89), HER (86), Lex (82)
- D grade (70–79): Tinder (72), OkCupid (73), Grindr (75), Ashley Madison (75), Plenty of Fish (71), Badoo (70), eharmony (72), and others.
Apps like Tinder and OkCupid are among the most downloaded globally, yet their security is mediocre at best.
And Ashley Madison — infamous for its catastrophic 2015 breach — still earns just a D nearly a decade later.
Worst performers
Five apps scored an F, placing them in the highest-risk category.
- Coffee Meets Bagel: Score 67, Grade F
- Christian Mingle: Score 66, Grade F
- Match: Score 64, Grade F
- Zoosk: Score 59, Grade F
- AdultFriendFinder: Score 40, Grade F
In short, platforms with the most infamous breaches — Ashley Madison, AdultFriendFinder, Coffee Meets Bagel, Zoosk, Tinder — continue to lag in security.
Match Group apps (Tinder, OkCupid, Plenty of Fish, Match.com) account for a significant market share, yet all scored C or below.
No app reached an A, proving that security is not yet a competitive differentiator in this industry.
Lessons from past breaches and today’s warning signs
The security weaknesses visible in today’s dating platforms are not hypothetical. The same categories of flaws have already driven some of the most damaging breaches in the dating industry and beyond.
Email security weaknesses
Our scans show that Zoosk, Match, Lex, SilverSingles, HER, EliteSingles, Coffee Meets Bagel, and Christian Mingle all lack strong email authentication safeguards such as DMARC, SPF, and DKIM. These weaknesses expose users to phishing and brand impersonation.
This is not a minor concern: in 2022, Dropbox suffered a breach when employees were tricked by a phishing campaign, leading to source code theft. Weak email security at the provider level enables these kinds of attacks, harming both companies and their users downstream.
Unpatched software
AdultFriendFinder and DOWN show evidence of unpatched software vulnerabilities, including over a hundred outstanding issues at AdultFriendFinder alone.
History shows how devastating this pathway can be: the Equifax (2017) breach that exposed data on 147 million Americans stemmed from a single unpatched Apache Struts vulnerability.
Transport and TLS weaknesses
Seven major platforms — Badoo, Zoosk, AdultFriendFinder, Match, Grindr, Ourtime, and Ashley Madison — display high number of TLS configuration issues.
These weaknesses map directly to what researchers uncovered at Tinder (2018), where incomplete encryption allowed for the reconstruction of user actions.
Web application exploits
Eleven platforms, including Zoosk, AdultFriendFinder, Ashley Madison, Ourtime, Bumble, Taimi, Coffee Meets Bagel, Grindr, Match, and BlackPeopleMeet, show signals of weak web application configuration.
These indicators are consistent with the pathways attackers exploited at AdultFriendFinder (2016), where a Local File Inclusion bug opened the door to database exfiltration.
A parallel in another sector is the MOVEit Transfer (2023) crisis, where SQL injection flaws in web-facing software allowed mass exploitation across hundreds of organizations.
Credential exposure and password reuse findings
BDI’s analysis shows that credentials from past data breaches continue to resurface in newly compiled databases on the dark web, often packaged and sold as part of larger data sets.
Our scans track dark web marketplaces and breach repositories to detect whether credentials linked to company domains appear.
In the past 30 days alone, credentials tied to 76% of the companies analyzed were found in such databases.
In most cases, the number of exposed accounts was relatively small—typically under 100 per company—and we cannot confirm whether those credentials remain valid. Our scans flag the presence of company-linked email domains in breach data and do not automatically imply that the company was breached.
Beyond exposure, we also measured password reuse. By tracking repeated password hashes tied to the same users across multiple breaches, we found that 56% of companies had employees reusing passwords.
Human impact
The names hit the internet first—gigabytes of them—then the phone calls, then the shame. Six days after the Ashley Madison dump, John Gibson, a New Orleans pastor and seminary professor, died by suicide. In interviews, his family said he left a note that mentioned depression and the breach; they believed he feared losing his job. It is one of the few cases where relatives have publicly connected a death to a dating-site breach with devastating clarity.
Police said there were more. At a press conference in Toronto, investigators announced they were looking into two unconfirmed suicides potentially linked to the leak and warned of an immediate wave of scams and extortion aimed at newly exposed users.
Within days, UK family-law reporters documented the first divorce case filed after a spouse found a partner’s details in the dump. Lawyers noted that even where adultery wasn’t provable, being registered on the site could meet the threshold for “unreasonable behaviour,” a common ground for divorce in England and Wales at the time.
Extortion arrived as predictably as spam. Criminals scraped the leaked emails and began sending tailored threats: pay in bitcoin or we'll tell your spouse, your boss, your congregation.
Ashley Madison remains the best-documented case regarding the consequences of leaked dating app data; however, it could be inferred that other leaks, like the AdultFriendFinder case, also had similar consequences, even if they weren’t made public.
What makes these breaches so corrosive isn’t just scale; it’s context. Dating and hookup platforms collect metadata that can be extremely damaging to a person's personal life—transaction history, messages, location hints, even kinks. When that metadata becomes searchable, strangers can weaponize it.
Impact on platforms
What happens to a dating platform after its secrets spill? In most cases, not much is publicly measurable. Outside of Ashley Madison, we found no credible, audited disclosures of traffic or user-base collapse tied directly to a breach across the major apps we reviewed.
Ashley Madison is the outlier. Similarweb estimates show traffic falling by roughly 80–90% in the months after the 2015 leak.
The company pushed back, claiming the scandal paradoxically juiced demand—“hundreds of thousands” of new sign-ups in the first post-leak week. Independent outlets reported these statements, but no audited subscriber or revenue figures were released.
The leak also revealed something users suspected long before the breach: the leaked list of names appeared to show over 95% male members. Regulators later alleged that Ashley Madison had used fake female profiles to spur spending (the “fembot” problem) before and around the breach era — deception claims the company settled with the FTC and several U.S. jurisdictions in 2016.
Reviews on Trustpilot even now continue to feature complaints about bot-like behavior.
Still, every major dating service hit by a high-profile leak in the last decade is still operating, and hard numbers on post-incident revenue or profit impact remain largely undisclosed.
In practice, reputational damage is obvious; quantifying it, much less tying it to churn or cash flow in public filings, almost never happens.
Emerging threat: fraudsters use AI to catfish
Issues in the online dating sector are evolving beyond traditional threats. Fraudsters now use chatbots and deepfakes to operate catfishing at scale, making scams harder to detect.
AI tools allow scammers to generate highly realistic photos, videos, and even live deepfake calls that mimic real people. Unlike older scams, which often relied on poorly written messages or stolen stock images, these AI-enhanced personas appear authentic and can sustain long-term conversations without raising suspicion.
According to the latest FBI annual report, losses from romance scams in the U.S. reached $672 million in 2024.
In December 2024’s PBA, the FBI warned citizens that criminals increasingly use generative AI to facilitate financial fraud, with romance scams being mentioned as one of the most common attack vectors.
As a result, victims are manipulated into trust faster and on a greater scale than ever before.
Policy and regulatory outlook
- Under GDPR, data collected by dating apps, like sexual orientation, is treated as “special category” information, thus requiring extra scrutiny when handled.
- Similarly, according to the California CPRA, sexual orientation is under the “sensitive personal information” category, which places such data under stricter regulations.
- Regulators are also examining “dark patterns” in dating apps, including a recent $14 million settlement with Match Group (Tinder, Match.com, Hinge, etc.) for deception in cancellation policies and subscription behaviour.
Practical security tips for dating app users
- Use a unique email just for dating apps. Keeps breaches from linking to your personal/work accounts.
- Avoid reusing profile photos. Prevents reverse-image searches from tying your dating profile to your identity.
- Be cautious with “login with Facebook/Google.” Safer to create a standalone login.
- Limit location sharing. Disable “precise” GPS tracking to reduce stalking risk.
- Don’t link social media accounts. Less data exposure if the platform is compromised.
Conclusion
Our findings show that many dating platforms in 2025 still have the same weaknesses that have driven devastating breaches. Unless corrected, history might repeat itself.
About Business Digital Index
The Business Digital Index (BDI) is a cybersecurity reputation platform that provides organizations with a real-time security rating based on publicly available data. It continuously monitors external digital assets — such as exposed systems, outdated technologies, and other risk indicators commonly targeted by threat actors — and evaluates them using a weighted scoring model. This model considers technical vulnerabilities and real-world attack patterns to deliver a clear, standardized view of your organization's external cybersecurity posture.
Get your Business Digital Index report
Take a moment to understand how your company appears to the outside world. This report uses verified public data to highlight potential risks.